UPDATE: $7.7 Billion Update to Patent Perspectives Report (Intel Acquires McAfee)
MIT's Technology Review's July - August issue includes anin-depth briefing on information security. In working with Technology Review, we assessed over 20 companies identified by Technology Review's editors across a spectrum of activities to support this briefing and to provide a supplemental report on key patent drivers and on patent positions in the industry.
Download a copy of the Patent Perspectives: On Security briefing
As information and infrastructure security continues to increase in personal, commercial and public importance, it is informative to understand how leaders in the field drive continuous innovations and derive value from the many strategic options available to them.
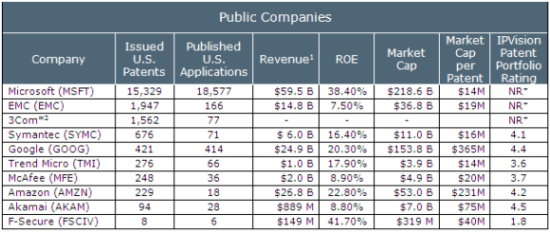
The supplemental report to Technology Review's Security Briefing reports key financial and patent metrics, including our Patent Portfolio Assessment ratings, for the following publicly listed companies ranging from broad-based software firms such as Microsoft to focused firms such as Symantec and McAfee:
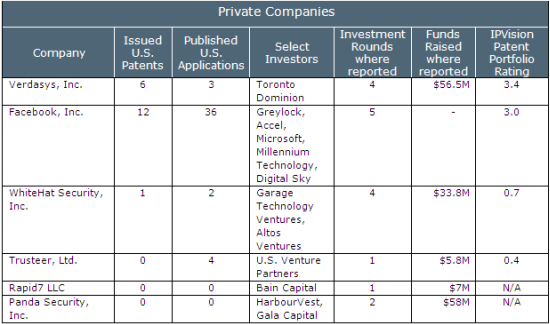
This analysis was extended to include ratings of venture capital funded companies, ranging from such well-known firms as Facebook to Verdasys, WhiteHat, and Panda Security:
As you read the report, we encourage you to consider the available key insights into questions such as:
• What U.S. patents do these 20 Companies own in the security space?
• What is the relative strength of their respective portfolios?
• How are these patent portfolios positioned in the broader patent landscape?
And, perhaps most importantly, consider the initial insights into how effectively management may be at utilizing intellectual property in their corporate strategy and in delivering financial returns.
In addition, to a focus on select companies, the supplemental report concludes with a direct comparison of the patent positions of two critically positioned companies: Symantec and McAfee.
There are many lessons that legal, R&D, and corporate leadership can garner from the forces shaping the security industry. Hopefully, you find the Security Briefing Technology Review and IPVision supplemental report useful your efforts.
On a closing note, to respect confidentiality and respect commercial interests, we relied exclusively upon Technology Review's identification of companies, topics, and public data in preparing this report. Please let us know if you have specific questions or if we can provide additional analysis based upon your more focused objectives.


